Cyberattacks on Local Governments and Agencies Are Unavoidable

Cyberattacks are inevitable. While many cybersecurity professionals focus on the first 24 hours of a cyberattack, appropriate preparation by state and local governments requires months of planning. Investing and adopting an approach that mitigates risk will make your eventual response more effective.
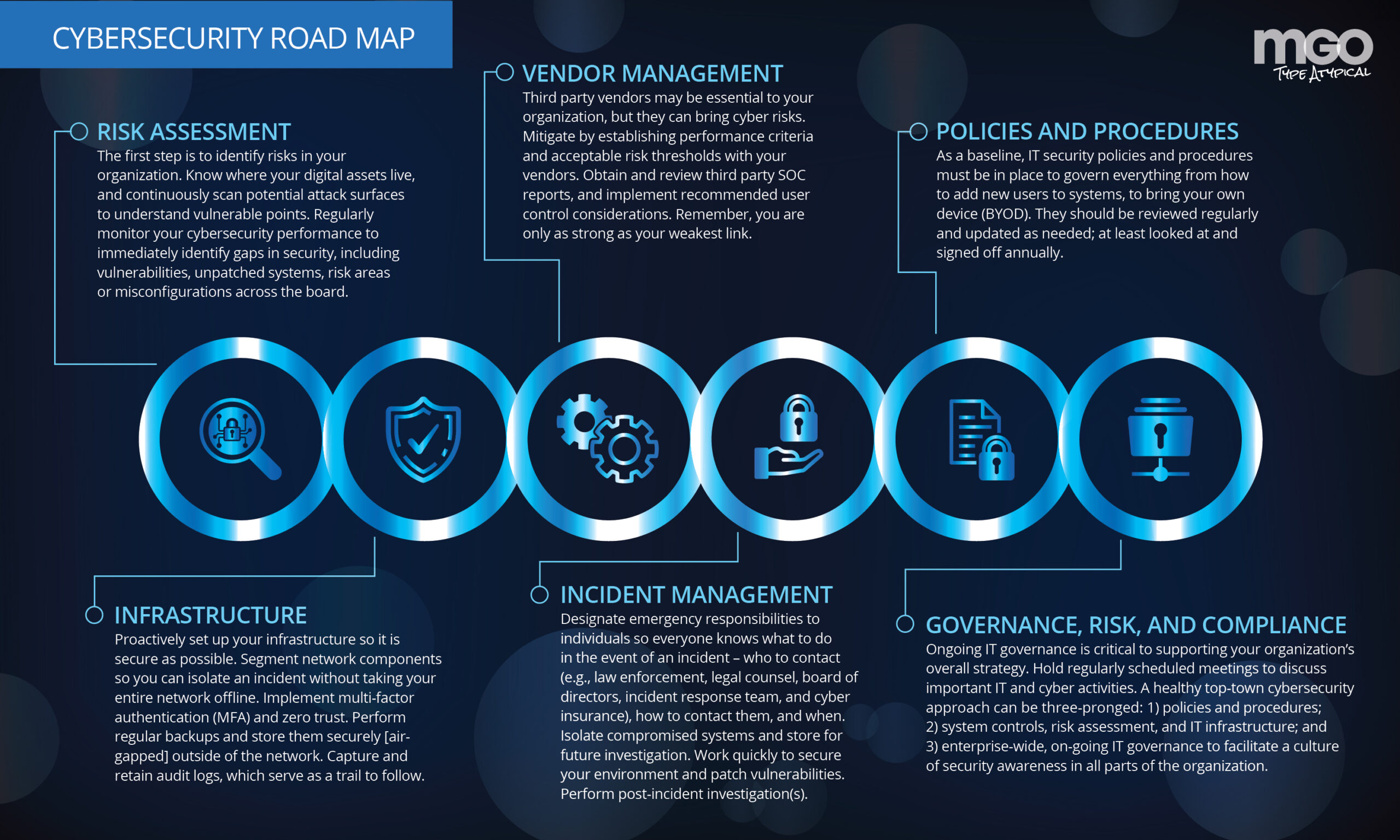
Proactive planning is vital
State and local governments are frequently constrained by their budgets. Proactive planning spreads both effort and budget into a longer timeframe, which allows investments to be made incrementally and resources to be consistently allocated.
Because cyberattacks are nothing new, many organizations have already prepared some sort of response plan. However, because the pace of cyberattacks and the sophistication of hackers is constantly increasing, your plan should be updated at least annually. A robust plan is a living document that involves cross functional teams that include IT professionals and leadership.
Risks should be identified and prioritized so that urgent needs can be addressed with immediate investments. Although, the complete (or updated) plan may never be complete, the prioritized pieces of it will form a framework through which cybersecurity becomes an ongoing conversation, and a lens through which daily work is viewed.
Have a contingency plan: know who to contact and how
A contingency plan should be in writing. The process of drafting a detailed plan that addresses many different scenarios is time consuming, and it is also necessary. The thought process and discussions that go into thinking through a robust response to a cybersecurity plan are valuable to the whole organization. When a cyberattack occurs, one of the greatest concerns is to stop the loss of sensitive information. Part of contingency planning will involve creating an information classification policy, so your information systems protect the highest value information with the highest level of security.
Contingency planning also involves a communication plan. In what order do you make phone calls to your incident response team, legal counsel, board of directors, insurance agent, or law enforcement? Who needs to know what, when? How do you document your actions?
If you think having these discussions is overwhelming and stressful in the planning stage, imagine what it would be like to try to make critical decisions when your firewall is open, your information systems are locked, and your daily work has come to a halt.
Update your system to reduce risk
State and local governments often have older IT systems, some of which have been in use for 20 years. These systems require patches to prevent cybercrime, and in most cases, the various information systems do not “talk” to each other.
One of the first steps you can take is to update your information systems. Part of this may involve a discussion of a policy manual and potentially some training so that people are aware of the risks that are constantly evolving. A standing IT governance committee may initially be dedicated to the upgrade, and later take on the ongoing task of mitigating cyber risks throughout your organization.
Mitigating some of these risks might include reviewing your cyber insurance policies to ensure that you have adequate coverage for overall data recovery and the cost of business interruption. This committee should also review your backup policies and services to ensure reliable storage in a separate location that is tested periodically to ensure compliance with your contracts.
Prepare to respond to cyberattacks
State and local governments should expect to be targeted — they have access to large amounts of personal information and data. Thus, it is crucial to have a plan that can be immediately put into action to protect this sensitive information for the people and communities you serve. Your response within the first 24 hours of the breach is critical to minimizing damage. With proper planning, even an aggressive attack can be survived with minimal losses.
If your organization is not yet prepared for a cyberattack, or you are interested in proactive planning against a breach, schedule a consultation with the MGO Technology Group or learn more about the services we provide here.