Key Takeaways:
- Understaffed teams increase cybersecurity risk and compliance gaps.
- Strategic outsourcing can reduce exposure without inflating headcounts.
- Cybersecurity assessments help prioritize the most impactful actions.
—
If your organization is facing tighter budgets and a leaner cybersecurity team, you’re not alone.
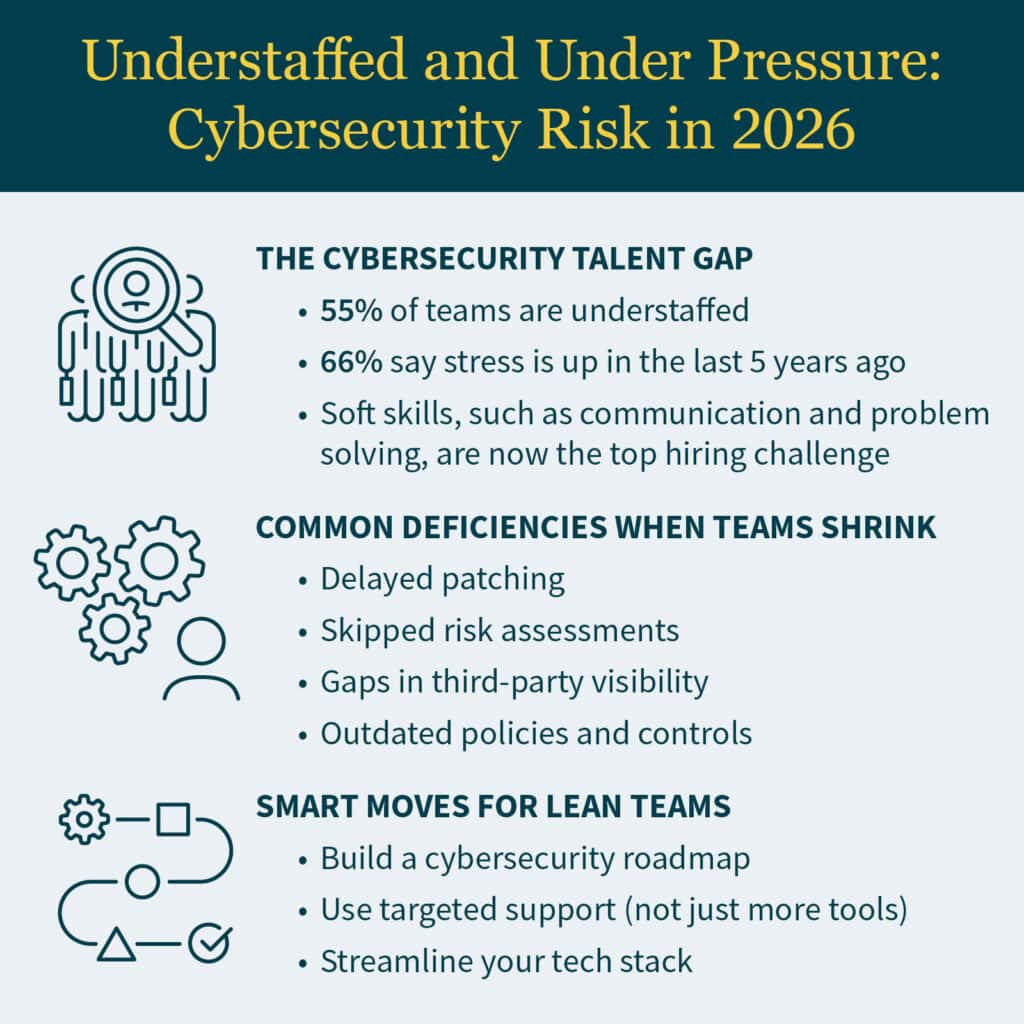
According to ISACA’s State of Cybersecurity 2025 report, 55% of cybersecurity professionals say their teams are understaffed while two-thirds report higher stress levels than five years ago — all amid rising cyberattacks and growing compliance demands.
Being short-staffed doesn’t just mean heavier workload; it introduces greater exposure to cyberthreats, raises the risk of missed compliance deadlines, and slows incident response — creating vulnerabilities that adversaries are quick to exploit.
But here’s the good news: Improving your security posture doesn’t always require adding headcount. Practical, strategic steps can help you optimize resources, strengthen defenses, and build resilience, even in a constrained environment.
Why Understaffed Often Means Under-Defended
Cybersecurity is a team effort — and when resources are limited, critical responsibilities often fall behind.
This typically shows up as:
- Security alerts being deprioritized or overlooked
- Patching schedules getting delayed
- Risk assessments falling off the roadmap
- Third-party monitoring becoming inconsistent
- Policies and procedures becoming outdated or under-reviewed
These delays can result in a growing backlog of unmanaged risk — one that compounds over time and becomes increasingly difficult to remediate.
When Risk Turns Into Business Impact
Even with a strong internal team, staffing constraints can create gaps in key areas including:
- Cloud infrastructure oversight, leaving misconfigurations or shadow IT unchecked
- Vendor contracts without clear security standards, increasing third-party risk
- Response plans that aren’t reviewed or tested regularly, slowing recovery during an attack
- Staff training and certifications postponed due to budget or time
These challenges can lead to vulnerabilities that impact your operational continuity, compliance standing, and client trust. Proactively addressing these gaps through streamlined processes, automation, and strategic partnerships helps your organization maintain resilience, even under resource constraints.
Industry Insight: Biotech
For biotech companies, the stakes are especially high. Lean teams managing sensitive intellectual property (IP) or clinical trial data may struggle to maintain continuous compliance with good practice (GxP) regulations, the Health Insurance Portability and Accountability Act (HIPAA), or Title 21 of the Code of Federal Regulations, Part 11 (21 CFR Part 11).
Without ongoing assessments or current documentation, critical timelines and funding may be impacted. Engaging external cybersecurity advisors with knowledge of biotech data integrity standards can provide structure and support when internal capacity is limited.
What You Can Do — Even With Limited Resources
If hiring isn’t an immediate option, you can still make progress by focusing on these key areas:
1. Build a Clear Cybersecurity Roadmap
A structured plan helps your team prioritize actions that reduce the most risk. Start with a focused cybersecurity program strategy and risk assessment to:
- Find your biggest gaps
- Align with frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) or System and Organization Controls (SOC) 2
- Set achievable short- and long-term security goals
- Communicate needs to stakeholders with data
With a roadmap in place, you can distribute internal and external resources where they’ll have the greatest impact.
2. Augment Key Functions With Support
Not every cybersecurity function needs to be handled in-house. External support can help you manage risk more effectively and stay current with evolving threats.
High-impact areas where outside support often helps include:
- Vulnerability management
- Ransomware readiness assessments
- Incident response planning
- Policy and procedure updates
This approach helps fill operational gaps without long-term staffing commitments.
3. Streamline Tools for Better Visibility
Managing too many security tools can lead to alert fatigue, duplicated effort, and unclear reporting. A technology rationalization review can help you:
- Find opportunities to streamline overlapping tools
- Improve monitoring coverage across cloud and hybrid environments
- Simplify internal reporting for management or board oversight
- Refine spend and usage across your toolset
Fewer tools — used more effectively — often produce better results.
Smarter Cybersecurity Starts Here: How MGO Supports Lean Teams
At MGO, we work with middle-market organizations to help them build and strengthen cybersecurity programs in ways that align with internal capacity and evolving requirements — even with lean internal teams.
Our cybersecurity and IT risk services include:
- Cybersecurity program strategy and roadmap
- Third-party risk management
- Compliance readiness — including HIPAA, SOC 2, Cybersecurity Maturity Model Certification (CMMC), and International Organization for Standardization (ISO)
- Vulnerability management and ransomware assessments
- Policy, governance, and awareness training
- Technology rationalization and cloud security review
We support organizations in biotech, cannabis, technology, media, and manufacturing with cybersecurity solutions designed to align with operational realities, resource availability, and regulatory expectations.
Let’s explore how you can strengthen your cybersecurity foundation.