Key Takeaways:
- Recent ransomware attacks in Minnesota and Nevada highlight growing risks for state and local governments.
- Limited budgets, legacy technology, resource gaps, and inadequate training create vulnerabilities that threat actors exploit.
- Strategizing, strengthening training, testing incident response plans, and managing third-party risk are essential next steps.
—
When cyberattacks struck the city of St. Paul, Minnesota, and the state of Nevada this past summer, the impacts underscored how vulnerable public systems can be. In St. Paul, the attack disrupted city operations — from phone lines and water bill payments to library services. In Nevada, hackers accessed thousands of files and triggered a statewide outage that shut down agencies like the DMV. These incidents made one thing clear: cybersecurity isn’t just an IT issue — it’s a public service issue that directly affects your community.
Across the country, state and local governments are increasingly being targeted by cybercriminals. Some attacks come from organized hacker groups, while others are believed to be nation-state sponsored. Either way, they share a common goal: exploiting weak points in your systems, processes, or personnel.
In many cases, your teams are being asked to do more with less — maintaining critical systems with flat or declining budgets. That makes it harder to recruit skilled cybersecurity talent, replace aging infrastructure, and implement modern defense tools. Yet, as the recent attacks show, protecting your digital infrastructure is now essential to maintaining public trust and continuity of service.
5 Insights to Strengthen Your Government’s Cyber Defenses
The fallout from these attacks offers valuable insights for any state or local government seeking to strengthen defenses and maintain resilience. Here are five lessons you can apply now to protect your systems, your operations, and the community.
1. Recognize the Human Impact
Cyber incidents in the public sector have a unique consequence: they disrupt real lives. When systems go offline, citizens can’t pay utility bills, access benefits, or get emergency support. That’s why cybersecurity planning must start with understanding the human impact.
Unlike private companies that may lose revenue, most of your organization’s “customers” are residents relying on essential services. This means every downtime event — whether caused by ransomware or system failure — directly affects public safety and well-being.
As the Nevada and St. Paul cases showed, cyber resilience isn’t just about restoring data. It’s about restoring public confidence.
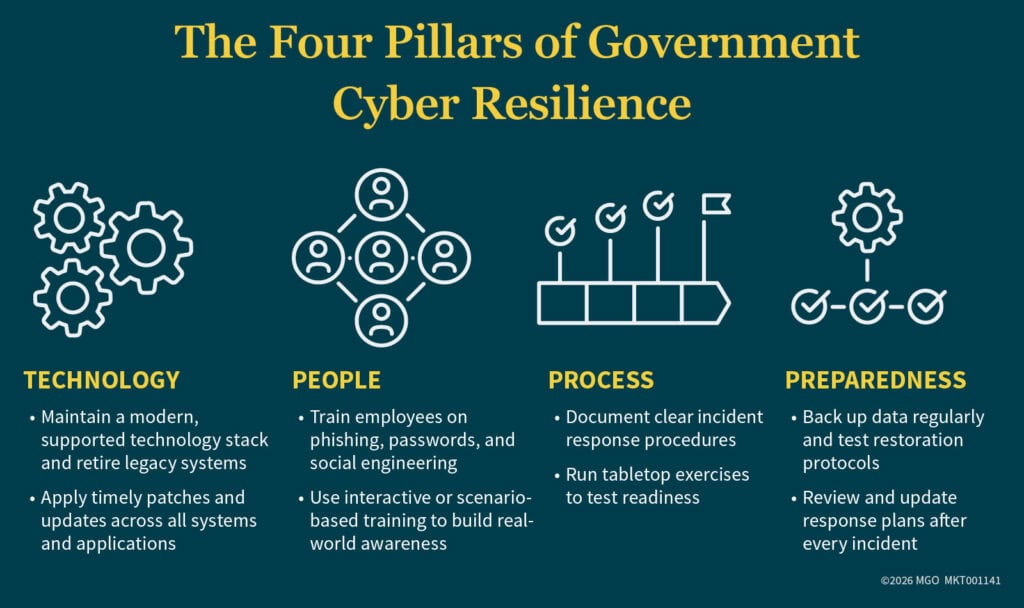
2. Focus on People, Process, and Preparedness
Technology alone can’t prevent cyberattacks. The most effective defense starts with people — and how well they’re trained to recognize and respond to threats.
Every employee is a potential target. Phishing and social engineering remain top entry points for ransomware, often because staff “click through” mandatory training without real engagement. Instead of relying on passive awareness programs, consider interactive or scenario-based sessions that simulate real threats.
Encourage staff to go beyond spotting suspicious emails and start asking deeper questions: Does this message make sense for my role? Why am I being asked to click this link or share this data? That contextual awareness can turn your workforce from a vulnerability into your first line of defense.
Preparedness also means knowing how to respond when — not if — a breach occurs. A well-documented and tested incident response plan can significantly limit damage. St. Paul’s response provides a strong example: by quickly identifying the intrusion and taking systems offline, the city prevented the attack from spreading across departments.
Regular tabletop exercises can help your team practice decision-making in real time — identifying who to contact, which systems to isolate, and how to communicate with the public.
3. Leverage Mutual Aid for Cyber Response
Many municipalities already have mutual aid agreements for fire, police, and emergency services. It’s time to extend that model to cybersecurity.
When St. Paul was attacked, it received assistance from the state and even the National Guard’s cyber units. Similar regional cooperation can help smaller governments recover faster. Establishing formal agreements before an incident occurs can give you access to expertise and resources you may not have in-house.
Consider coordinating with neighboring jurisdictions, state agencies, and trusted vendors to define roles, response protocols, and communication channels. A networked approach strengthens everyone’s defenses.
4. Manage Third-Party and Supply Chain Risks
Even if your own systems are secure, vulnerabilities likely exist within your vendors’ networks. Cities and counties often rely on hundreds of applications and service providers — from payment systems to data hosting platforms.
Every one of those vendors has its own subcontractors and software dependencies, multiplying your potential exposure. A single misconfiguration in a vendor’s system can provide attackers with a gateway into your environment.
Proactive vendor risk management is critical. Start by mapping all third-party connections to identify who has access to your systems and data. Then establish clear security expectations through contracts, periodic reviews, and automated monitoring tools. Affordable solutions now exist to continuously scan vendors for known vulnerabilities, giving you real-time visibility into your external risk landscape.
5. Address Legacy Technology and Resource Gaps
Many governments still rely on outdated hardware and software — not because of negligence, but because of limited funding and competing priorities. Unfortunately, “tech debt” becomes a growing liability over time. Unsupported operating systems and unpatched applications are prime entry points for attackers.
Transitioning to cloud-based systems can help, but even modern platforms require ongoing configuration, monitoring, and updates. Build technology lifecycle planning into your budget process and make cybersecurity a recurring line item, not a one-time expense.
At the same time, recognize that public sector salaries often can’t compete with private industry. Consider creative staffing solutions like fractional cybersecurity leadership or shared services across municipalities to close the skills gap without overextending budgets.
Move From Reaction to Resilience
Cyber threats aren’t going away. Ransomware remains the top choice for malware, with third-party compromise being the top threat vector for delivery. Artificial intelligence is now amplifying these risks by automating phishing campaigns and impersonation attempts at massive scale.
The path forward isn’t just about prevention — it’s about resilience. By combining awareness, preparation, collaboration, and modern risk management, you can limit the impact of inevitable incidents and recover faster.
You don’t have to face these challenges alone. The key is to start where you are, identify your most critical gaps, and take actionable steps toward a stronger, more secure future.
How We Can Help
MGO’s State and Local Government team provides cybersecurity assessments, readiness testing, and consulting support tailored to your agency’s needs. Whether you need help identifying risks, improving response plans, or managing third-party vendors, we can help you strengthen your defenses and protect your community.
Reach out to our team today to start building your cybersecurity roadmap.